Agent Monitor
Agent Monitor rules
Create rules to detect and block dangerous agent actions. Access rules at Agent Monitor Rules.
Built-in detection
| Category | What it detects |
|---|---|
| Secrets | API keys, access tokens, credentials being sent to models |
| PII | Personally identifiable information in agent interactions |
| Prompt injection | Potential injection attempts in prompts |
| Tool permissioning | Unauthorized tool access attempts |
Custom rules
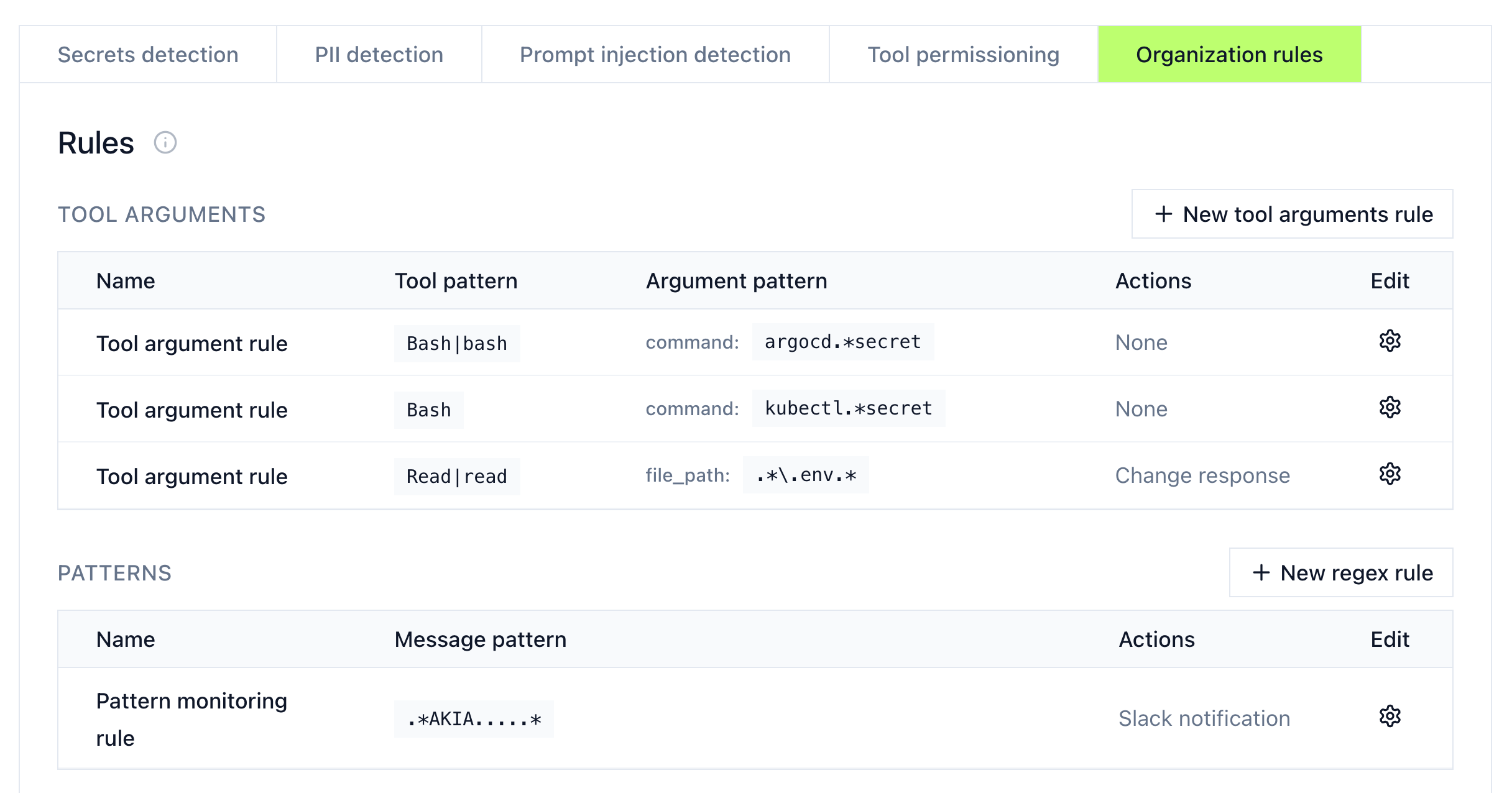
Create organization-specific rules under the Organization Rules section.
Tool arguments rules
Match tool calls with specific argument patterns:
- Click + New tool arguments rule
- Set the tool pattern (e.g.,
Bash,Read|read) - Define argument conditions (e.g.,
command: kubectl.*secret) - Choose an action
Pattern rules
Match message content using regex:
- Click + New regex rule
- Define the pattern to match
- Choose an action
Actions
| Action | Effect |
|---|---|
| None (flag only) | Logs the action without blocking. Review at Live Activity. |
| Change response | Modifies the tool call to prevent execution |
| Slack notification | Sends an alert to a Slack channel |
Manage rules
Edit or delete rules using the settings icon next to each rule.