MCP Gateway
Add a remote MCP
Connect to an MCP server that already runs in your infrastructure or is hosted by a vendor—MintMCP applies gateway-level authentication, authorization, and logging while treating the remote endpoint as the source of truth.
When to use remote MCPs
- SaaS providers that publish their own MCP endpoints (e.g., a vendor's official MCP)
- Internal services your organization already hosts outside MintMCP
- Partner-provided MCP endpoints
Adding a remote MCP
- Navigate to MCP store in the MCP gateway sidebar
- Click + Add MCP
- Select Add Remote MCP
You'll configure two settings:
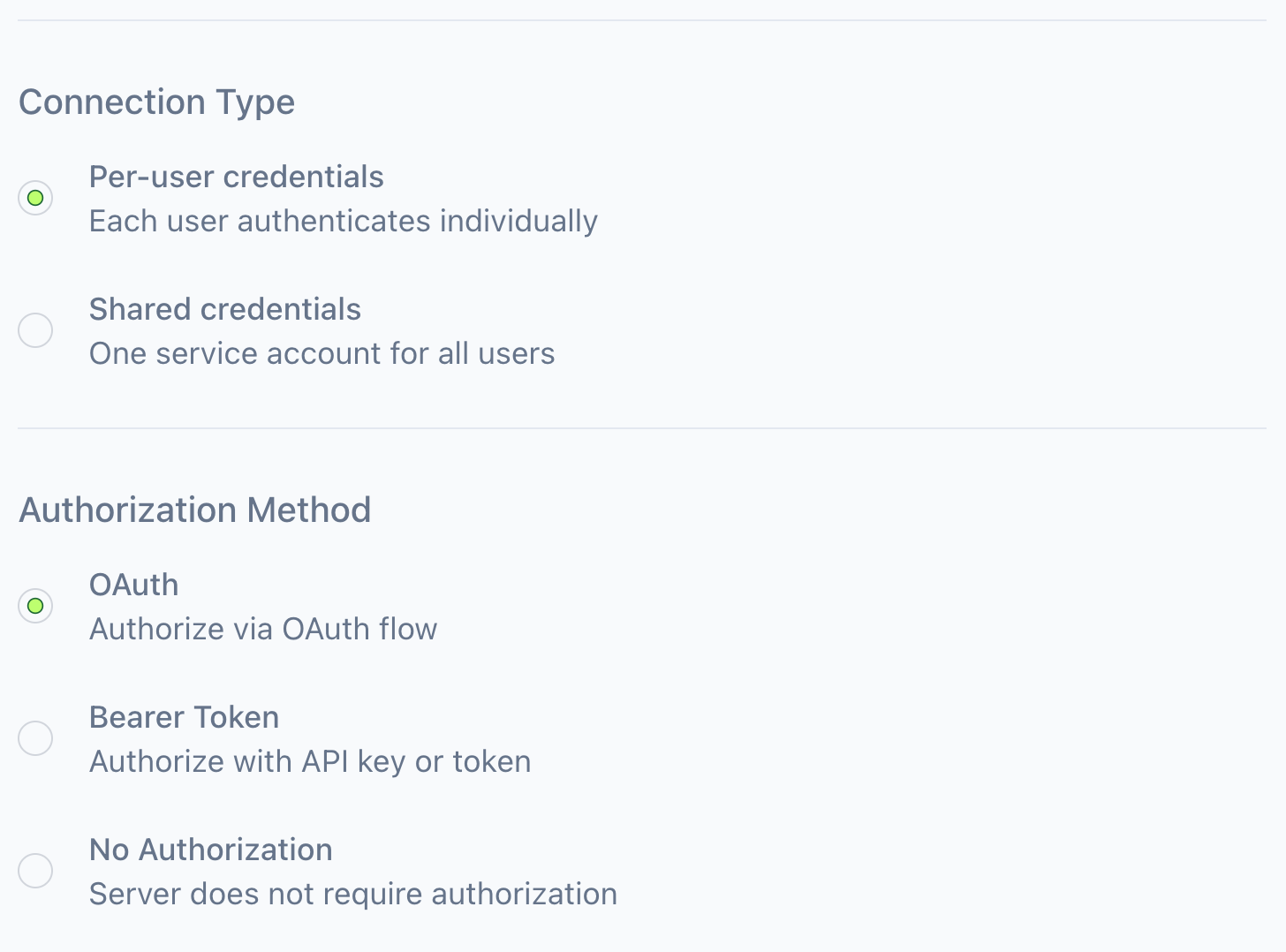
Connection type
Determines how credentials flow to the MCP server:
| Type | Description | Use when |
|---|---|---|
| Per-user credentials | Each user authenticates individually with the remote service | Users need personal access (email, calendars, documents, or any service with user-specific permissions) |
| Shared credentials | One service account for all users | Read-only data sources, shared knowledge bases, or internal systems without per-user auth |
Authorization method
Specifies how the MCP server authenticates requests:
| Method | Description |
|---|---|
| OAuth | Authorize via OAuth flow (most common for per-user credentials) |
| Bearer token | Authorize with API key or token |
| No authorization | Server does not require authorization |
How credentials work
MintMCP stores credentials securely and brokers them to the remote server, so members authenticate once with MintMCP (using OAuth) and get per-user attribution for all tool invocations.
For per-user credentials:
- User connects to the MCP server through MintMCP
- MintMCP prompts them to authenticate with the remote service
- Credentials are stored securely and used for subsequent requests
For shared credentials:
- Admin provides the service account credentials once
- All users share the same credentials when accessing the MCP server
Next steps
- Administration: Overview of managing MCP servers
- Tool customization: Configure which tools are exposed